Introduction
AWS recently released the IAM Roles Anywhere and its well thought and recommended feature instead of using Long term access keys for workloads. In short, AWS IAM Roles anywhere is based on x.509 certs by creating the trust between PKI and IAM.
Why I have to use AWS IAM Roles Anywhere?
Historically on-premise workloads access AWS resources via Long term access keys and one of the common requirement is to access the S3 bucket for upload/download artefacts but it increases the likelihood of compromised keys.
AWS IAM Roles Anywhere helps to mitigate the risk by providing short term credentials.
Configure AWS IAM Roles Anywhere with External CA
Below steps are involved for the setup
- Create CA (Existing CA will do) or AWS ACM PCA is also an option
- Create Trust Anchor (Establish trust between PKI and AWS IAM)
- Create and configure a role that trusts IAM Roles Anywhere
- Create Profile to use IAM Roles anywhere
- Create an Entity Certificate and sign with root CA
- Test the AWS IAM Roles anywhere
Create CA
For demonstration purpose , Self Signed Root CA is utilised for the demo . Avoid use of Self-signed Certs for real environment because its difficult to maintain.
CFSSL to create and sign CA and another option is openssl by following using this link https://docs.microsoft.com/en-us/azure/application-gateway/self-signed-certificates
Download the cfssl and cfssljson binaries from this github https://github.com/cloudflare/cfssl
CloudFlare SSL
{
"CN": "Demo Root Certificate Authority",
"key": {
"algo": "rsa",
"size": 2048
},
"names": [
{
"C": "Test",
"L": "Hello World",
"O": "Internal"
}
],
"ca": {
"expiry": "87600h"
}
}
cfssl genkey -initca csr.json | cfssljson -bare caCreate Trust Anchor
Upload the ca.pem to IAM Roles Anywhere by selecting the External certificate bundle. AWS IAM Roles anywhere found at the bottom of AWS IAM Roles screen
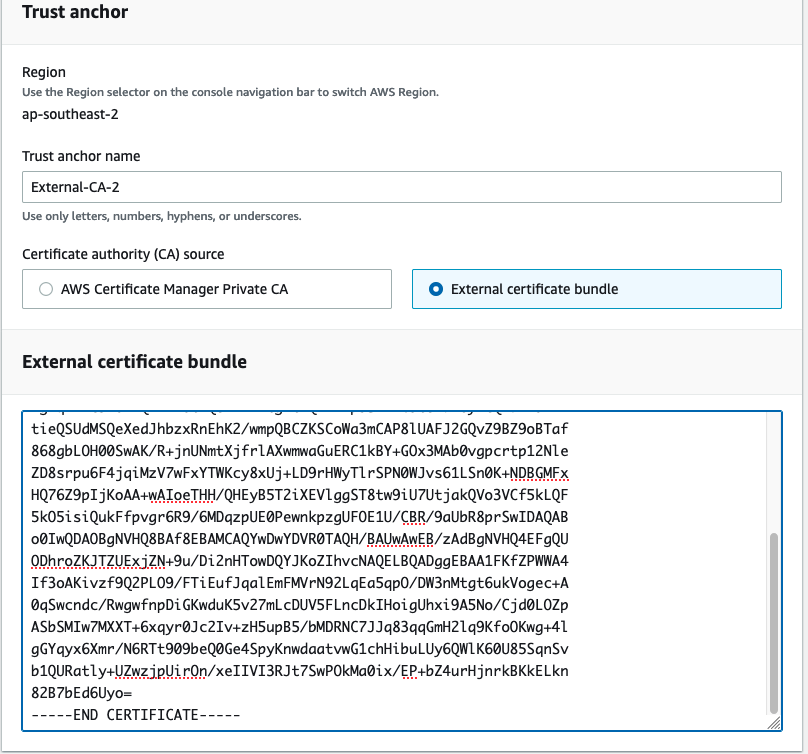
Create and configure a role that trusts IAM Roles Anywhere
Trust policy allows to assume the policy document by AWS IAM Roles Anywhere principal and able to access the AWS resources based on the permissions attached to the role
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Principal": {
"Service": "rolesanywhere.amazonaws.com"
},
"Action": [
"sts:AssumeRole",
"sts:SetSourceIdentity",
"sts:TagSession"
]
}
]
}https://docs.aws.amazon.com/rolesanywhere/latest/userguide/trust-model.html#trust-policy
Create profile to use IAM Roles anywhere
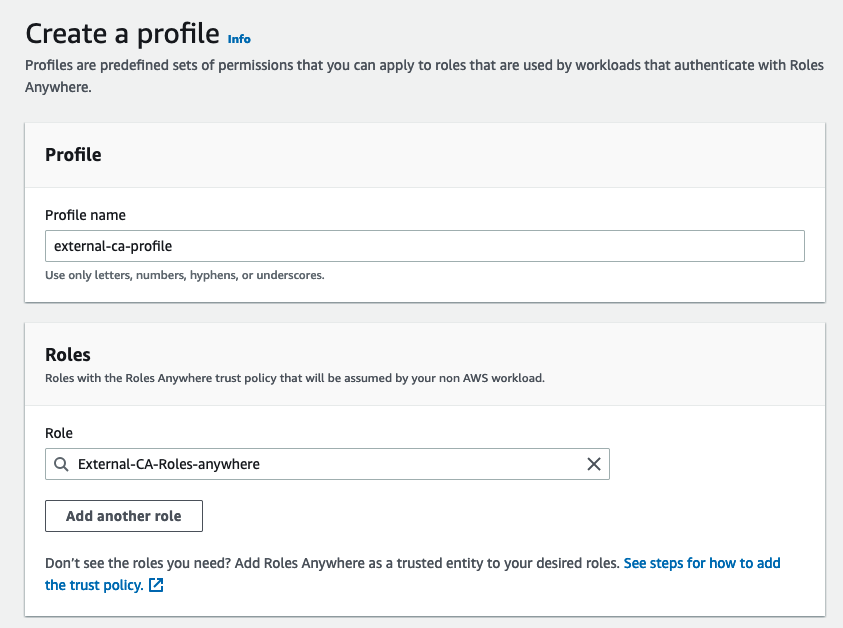
Create an Entity Certificate and sign with root CA
Generate the entity certificate for signing and sing it using previous created CA
cfssl genkey csr.json | cfssljson -bare signcsropenssl req -text -noout -verify -in signcsr.csr
verify OK
Certificate Request:
Data:
Version: 0 (0x0)
Subject: C=US, ST=California, L=San Francisco, O=Internet Widgets, Inc., OU=WWW, CN=demo_test
Subject Public Key Info:
Public Key Algorithm: rsaEncryption
Public-Key: (2048 bit)Sign the entity certificate using ca.pem
cfssl sign -ca ca.pem -ca-key ca-key.pem signcsr.csr | jq -r '.cert' > cert.pemopenssl x509 -in cert.pem -text -noout
Certificate:
Data:
Version: 3 (0x2)
Serial Number:
1a:3e:66:1e:c3:17:f6:a4:42:81:cb:67:41:f2:dc:f2:03:7e:09:81
Signature Algorithm: sha256WithRSAEncryption
Issuer: C=Test, L=Hello World, O=Internal, CN=Demo Root Certificate Authority
Validity
Not Before: Sep 5 01:58:00 2022 GMT
Not After : Sep 5 01:58:00 2023 GMT
Subject: C=US, ST=California, L=San Francisco, O=Internet Widgets, Inc., OU=WWW, CN=demo_test
Subject Public Key Info:
Public Key Algorithm: rsaEncryption
Public-Key: (2048 bit)AWS signing helper is helps to get the temporary credentials from AWS using signed certificate
https://docs.aws.amazon.com/rolesanywhere/latest/userguide/credential-helper.html
[profile demo]
credential_process = /home/ec2-user/iam-roles-anywhere/aws_signing_helper credential-process --certificate /home/ec2-user/self-signed-certs/demo/cert.pem --private-key /home/ec2-user/self-signed-certs/demo/signcsr-key.pem --trust-anchor-arn REPLACEME --profile-arn REPLACEME --role-arn REPLACEMEexport AWS_PROFILE=demo
aws sts get-caller-identityAdvanced Scenarios
Fine grained access to AWS IAM roles by using the condition statement . Subject CN=demo_test only assume the role.
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Principal": {
"Service": "rolesanywhere.amazonaws.com"
},
"Action": [
"sts:AssumeRole",
"sts:TagSession",
"sts:SetSourceIdentity"
],
"Condition": {
"StringEquals": {
"aws:PrincipalTag/x509Subject/CN": "demo_test"
}
}
}
]
}Conclusion
AWS IAM Roles anywhere is backed by PKI and its recommended approach for workloads outside of AWS to get access to short term credentials
“Views Expressed” Disclaimer
This disclaimer informs readers that the views, thoughts, and opinions expressed in the text belong solely to the me.