What are Canary tokens?
Canary tokens is simple way to detect attacker in your environment. Canary tokens provides visibility and able to identify how far the attacker penetrated the network. And also, sometimes it can be used to test your defence system. In the blog post, I am going to show how easy to deploy the AWS canary tokens.
I always compare Canary tokens with rat traps just keep it everywhere so you know where bad actors likes to show up in your network.
Setup
Based on this blog post, I have created canary token and place in it my aws config file location and its the same place where valid AWS API keys is usually kept.
Navigate to http://canarytokens.org/generate# and chose AWS Keys from the drop down and provide email address or webhook URL with meaningful description. Thats it ! I have got a token to catch the bad actor.
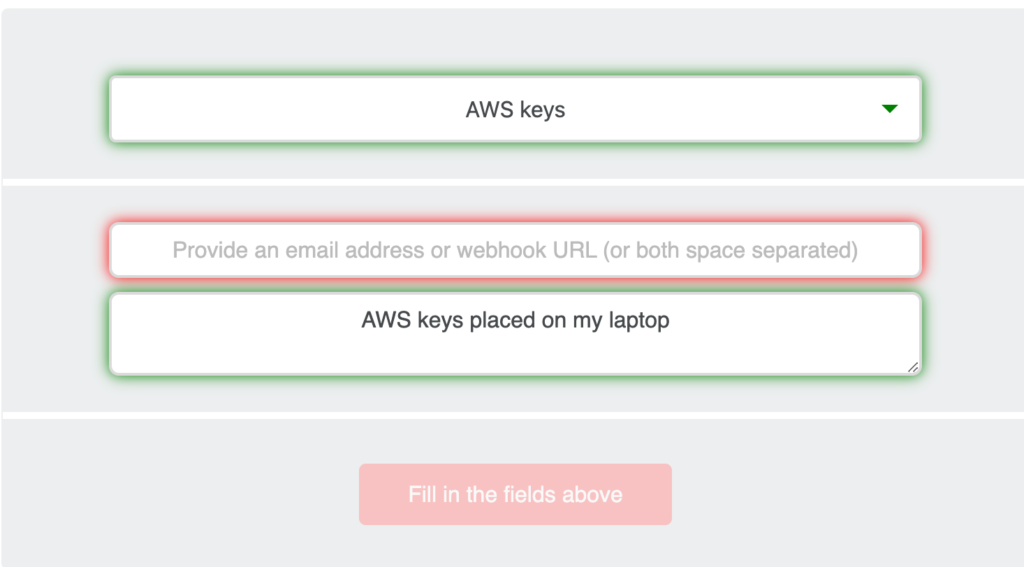
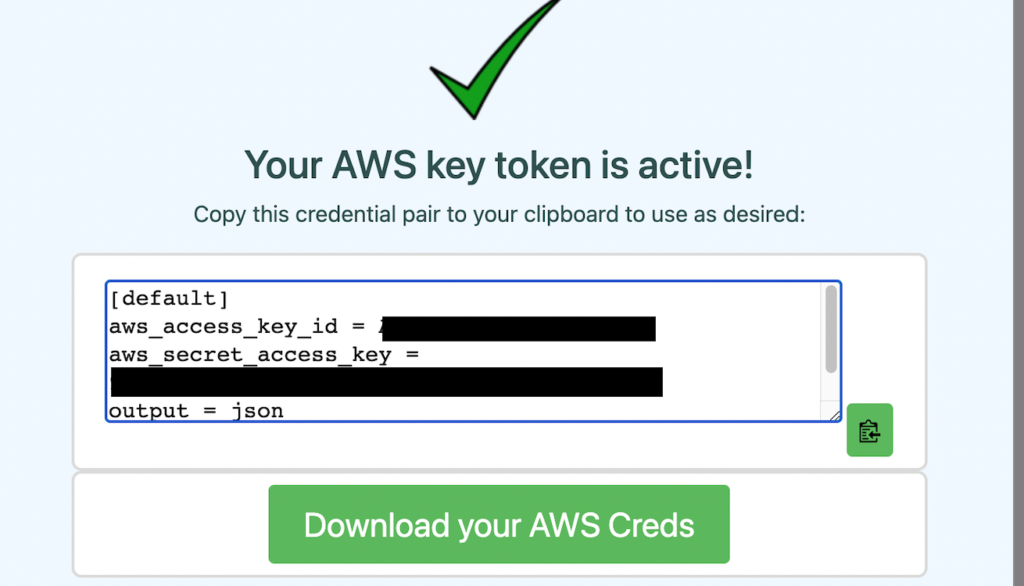
Next step is to download the AWS credentials file into ~/.aws directory
I have noticed downloaded credentials from site is having wrong key name so change the value from
aws_access_keytoaws_access_key_id
❯ ls ~/.aws/credentials
credentials
❯ cat credentials
[default]
aws_access_key_id=AKIAHELLOIAMHERE
aws_secret_access_key=9ceverythingintheworld
region=us-east-2
output=json%once its ready then test by executing normal aws cli commands and if its working you will get an mail from nominated email address. Some sample aws commands below to demonstrate the test
❯ aws s3 ls
An error occurred (AccessDenied) when calling the ListBuckets operation: Access Denied
aws sts get-caller-identity
{
"UserId": "AIDASP2TPHJSUHE7LPWIT",
"Account": "171436882533",
"Arn": "arn:aws:iam::171436882533:user/canarytokens.com@@26f0775shs8r5cd1v2sxeeoj4"
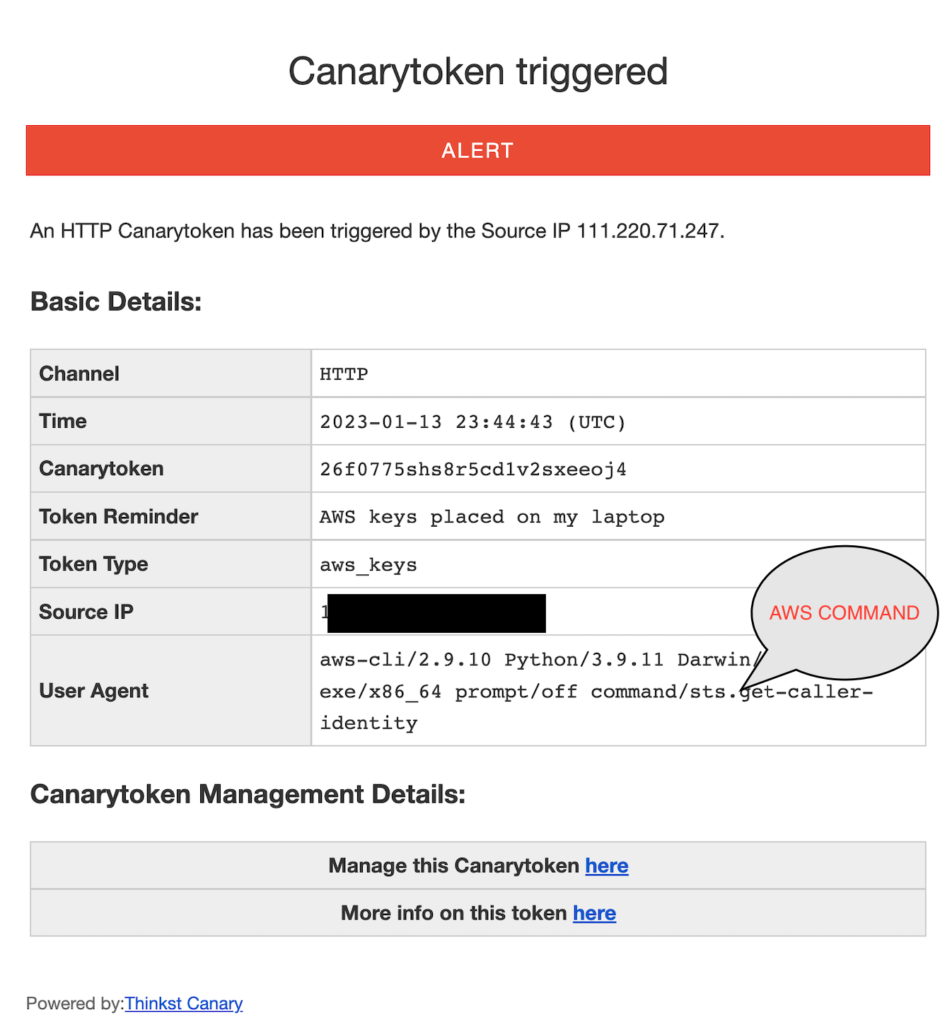
}As you can see tokens doesn’t give any access but however aws sts get-caller-identity provides clue what this token about and where it came from.
I got a mail in my inbox and its alert from Canarytoken triggered and all the setup took me less than 5 mins to create and deploy this canary tokens.Sweet!
Conclusion
Security shouldn’t be hard and it can be simple like using canary tokens to detect the bad actors in your network. Canary tokens are free to use with following benefits
- Detect bad actors in your network
- Test your defence system by identifying how far attackers breached your network
- Test your operating effectiveness of security tools