Introduction
Cyber Security Incident response is set of capability with set of purpose responding to computer security related problems.
Cyber Security Incident response team (CIRT) / Computer security incident response (CSIRT) is a group of skilled professionals assess the cyber security events and provide guidance or response to the events. Incident response is one of security pillar to protect the organisation’s from cyber security incidents. In this blog post, we discuss about the foundations of successful incident response and different activities around incident response.
What is incident Response?
Incident response is a combination of people, process and technology to effectively assess the cyber security events and recover from suspected cyber security compromise.
People – Incident Responders , Threat Intelligence Folks , Senior management and Employees.
Process – Playbooks and Runbooks
Technology – Security Incident and event management tool , Detection and analysis mechanism
Foundations of incident Response
As per NIST computer security incident Handling guide, incident respond contains four phase. Let’s explore each of the phases
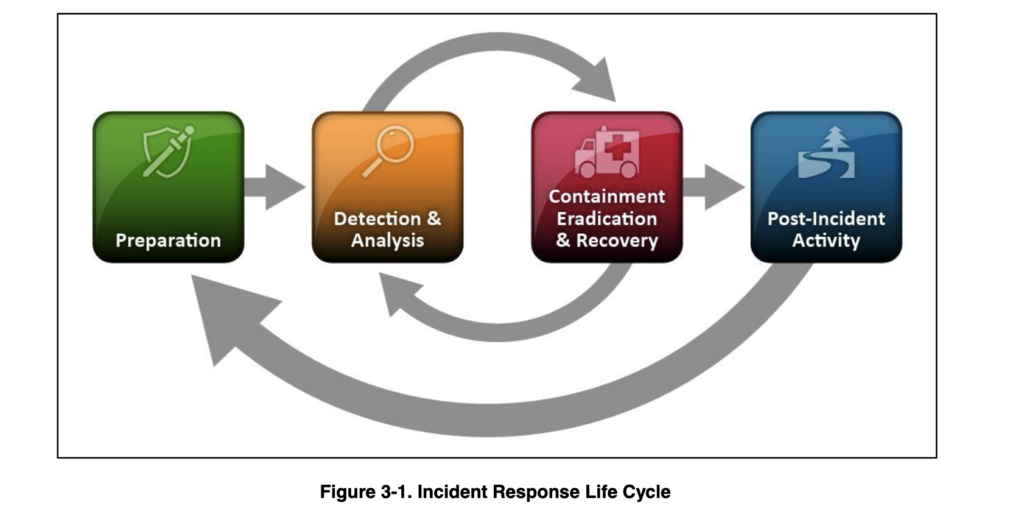
Preparation
In preparation phase, you prepare the people, process and technology to successfully respond to cyber security incidents. You will identify the people needs to be on-call, hands on keyboard and take actions. Create playbooks and runbooks for the each scenario. And designing emergency or break-glass access to the environment.
Playbooks / Runbooks is a documented set of procedures and automation to address specific scenario. For e.g. Playbook for ransomware, bit coin mining and DDOS attacks
Operations
Operations phase encompasses Detection & Analysis, Containment, Eradication & Recovery phases. In this phase, you act on active security incident meaning you detected security event on your favourite SIEM tool and determining whether the security incident is false or true positive. If its true positive then executing series of steps as pre-defined playbook to address the incident. And also in this phase you have to contain the incident as quickly and eradicate / restore the system to good working condition.
Post incident activity
Security incident response is not an one-time activity and goal is to learn from the past incidents and improve your preparations and operations phase if you find gaps. For example, if you identified some steps are missing to resolve the security incident then update the playbook with necessary steps.
Regularly conduct security game day, red team exercise and threat simulation activity to test your playbooks, run books, people and process.
Conclusion
There is a difference between seeing an alert and not seeing an alert. In order to successfully respond to security event then you or your team have mechanism to see an alert. So first step is to turn ON logging for all resources whether its cloud or on-premise or container or serverless workloads. Next step is to aggregate logs into central repository to run detection logic and also helpful to investigate actual security incident.
Reference from NISThttps://nvlpubs.nist.gov/nistpubs/specialpublications/nist.sp.800-61r2.pdf