In the previous post, I showed you how to create AWS IAM Roles Anywhere with external CA and in this post am going to discuss about some advance topics such as
- How to revoke a certificate
- How to restrict the user assuming IAM role based on subject CN value
- How to restrict the roles only from authorised networks
How to revoke a certificate
There are multiple scenarios where you want to revoke an entity certificates like compromised entity or during off-boarding of user. To demonstrate the certificate revocation I am going to use ACM PCA (AWS certificate Management Private certificate Authority) and the Certificate revocation is using certificate revocation list(CRL) or Online Certificate Status Protocol(OCSP) or both. IAM Roles anywhere has a limitation where it cannot talk to CRL provider’s directly so it has to be imported using CLI. Steps involved to revoke the certificate using CRL.
- Revoke the certificate from ACM PCA and the ACM PCA deposits the CRL certificate into Amazon S3 bucket
- Retrieve the CRL from the S3 bucket
- Import CRL to AWS IAM Roles anywhere
ACM PCA revocation
Login to AWS Console and navigate the ACM PCA to revoke a certificate. Copy the certificate id and serial number to revoke.
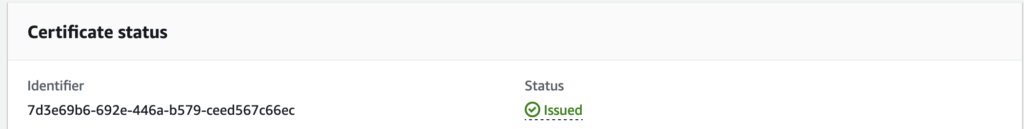
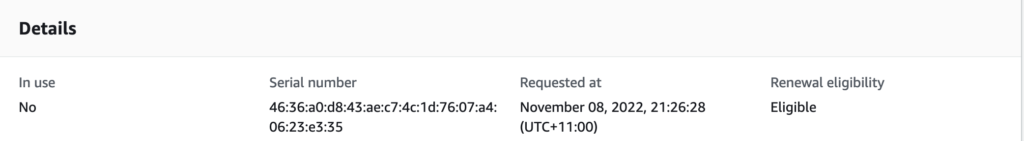
aws acm-pca revoke-certificate --certificate-authority-arn arn:aws:acm-pca:ap-southeast-2:<AWS ACCOUNT ID>:certificate-authority/4891e018-d1d9-4105-8118-0a01be7cf393 --certificate-serial <certificate serial number> --revocation-reason "KEY_COMPROMISE"After revoking the certificate from AWS PCA and CRL will be imported into S3 bucket. And the pre-requisite for revoking the certificate is to have AWS S3 bucket configured with access policies, BPA and encryption. More details for configuring CRL with ACM PCA
Retrieve the CRL from AWS S3 bucket
Download the CRL from S3 bucket
aws s3 cp s3://BUCKET_NAME/crl/4891e018-d1d9-4105-8118-0a01be7cf393.crl . openssl crl -inform DER -in 4891e018-d1d9-4105-8118-0a01be7cf393.crl -noout -text
Certificate Revocation List (CRL):
Version 2 (0x1)
Signature Algorithm: sha256WithRSAEncryption
Issuer: /C=AU/O=IAM Roles Anywhere demo/OU=STAM/ST=NSW/CN=IAM Roles Anywhere root CA/L=Sydney
Last Update: Nov 8 09:29:48 2022 GMT
Next Update: Nov 15 10:29:48 2022 GMT
CRL extensions:
X509v3 CRL Number:
1667903388536
X509v3 Authority Key Identifier:
keyid:6D:2D:9E:1D:76:3C:BD:5A:6B:9F:BC:7B:67:AB:2E:2A:C7:BE:F7:A8
Revoked Certificates:
Serial Number: 4636A0D843AEC74C1D7607A40623E335
Revocation Date: Nov 8 10:27:52 2022 GMT
CRL entry extensions:
X509v3 CRL Reason Code:
Key CompromiseImport the CRL to AWS IAM Roles anywhere
Steps to import the CRL to AWS IAM Roles anywhere
- create the PEM file from downloaded from S3 CRL bucket
- upload the CRL using
import-crlcommand - Enable the CRL using CLI and CRL is ready to use now
openssl crl -inform DER -in 4891e018-d1d9-4105-8118-0a01be7cf393.crl > revoke.pem
aws rolesanywhere import-crl --crl-data fileb://revoke.pem \
--name Revoke-CRL \
--trust-anchor-arn arn:aws:rolesanywhere:ap-southeast-2:XXXXXXX:trust-anchor/166bddfd-1ac1-4d0a-aa97-5b5b5b077db3
aws rolesanywhere list-crls
aws rolesanywhere enable-crl --crl-id <CRL Value>❯ aws s3 ls
Error when retrieving credentials from custom-process: 2022/11/19 19:04:36 AccessDeniedException: Certificate revokedHow to restrict the user assuming IAM role based on subject CN value
When you start signing the entity certificates with root CA all certificates have the same trust so one way to restrict some roles accessed by certain users is by adding condition in IAM trust policy.
{
"Version": "2012-10-17",
"Statement": [
{
"Sid": "",
"Effect": "Allow",
"Principal": {
"Service": "rolesanywhere.amazonaws.com"
},
"Action": [
"sts:AssumeRole",
"sts:SetSourceIdentity",
"sts:TagSession"
],
"Condition": {
"StringEquals": {
"aws:PrincipalTag/x509Subject/CN": "terraform.iamrole.test"
}
}
}
]
}And more ways to restrict the role access refer the documentation
How to restrict the access from authorised networks?
One way to restrict the access using session policies limit the permissions by the role’s permission policy
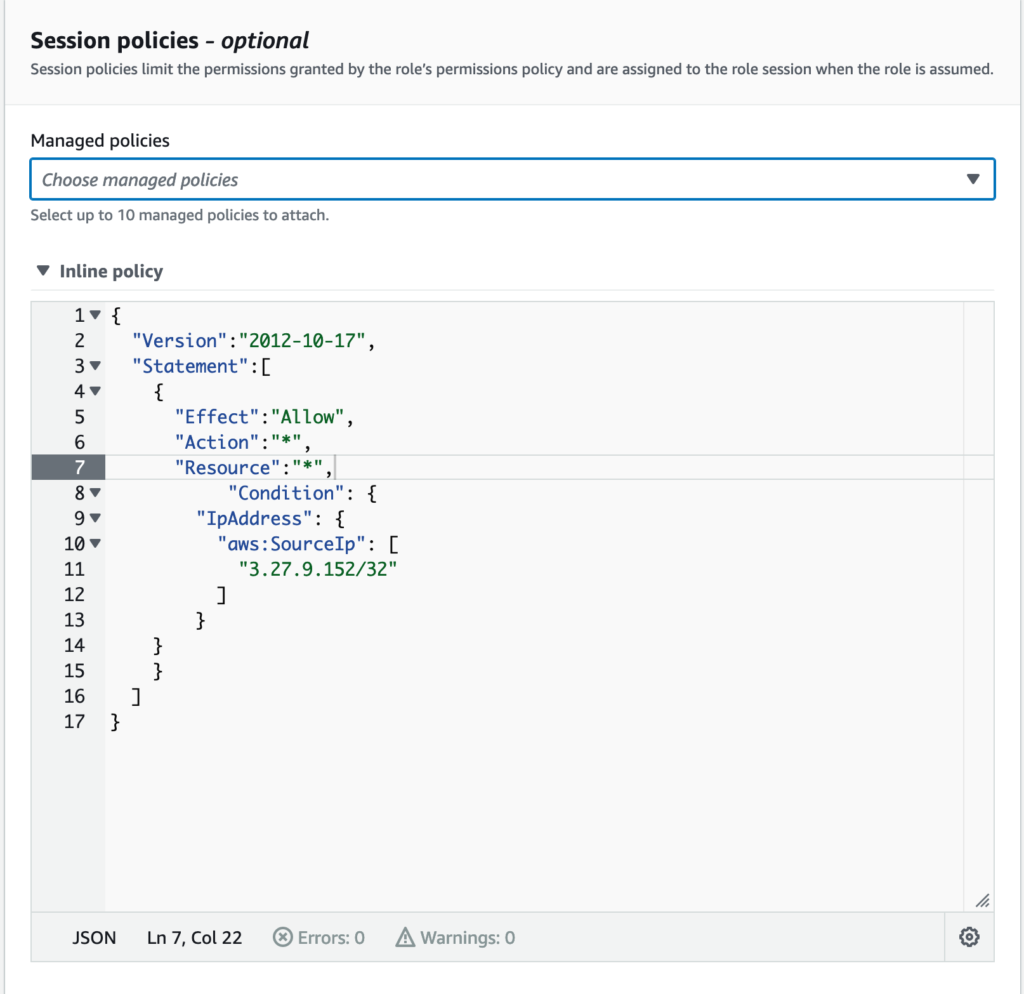
Conclusion
We have learnt how to achieve fine grained access based on user subject and CIDR address using trust policy and session policies respectively and also learnt how to revoke the certificate using CRL.
So IAM Roles anywhere is x.509 certificate based authentication provides mechanism to access AWS resources from on-premise or other cloud provider. Regardless, security controls is required to protect the certificate private keys using ACL and certificate issuances should be governed appropriately.